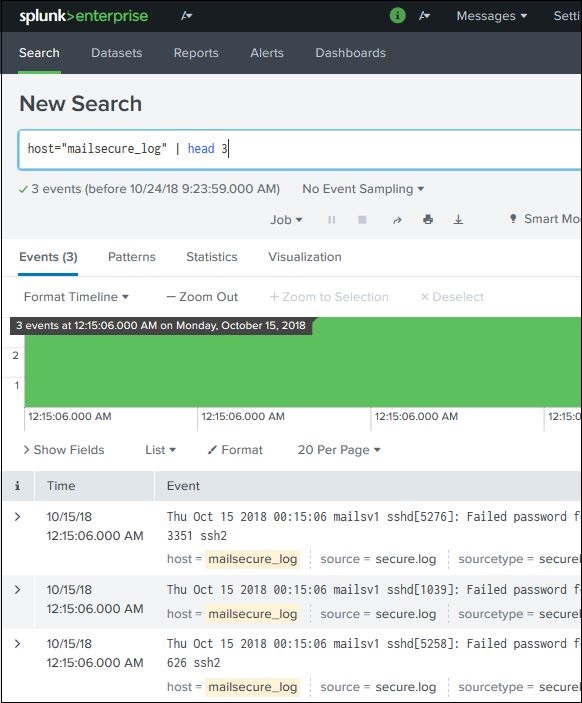
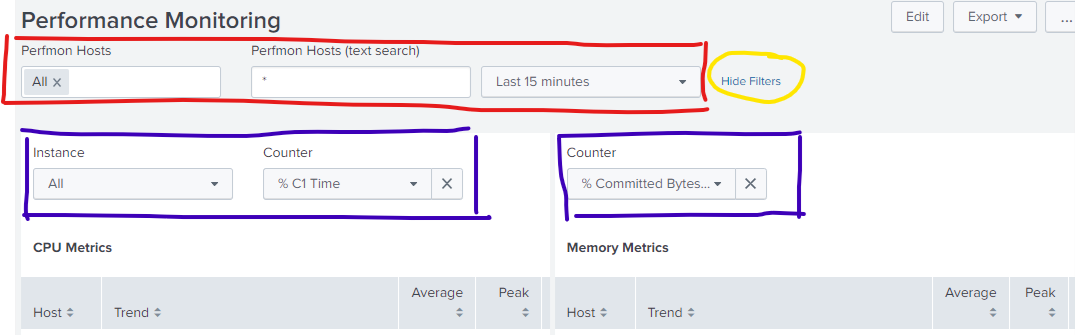
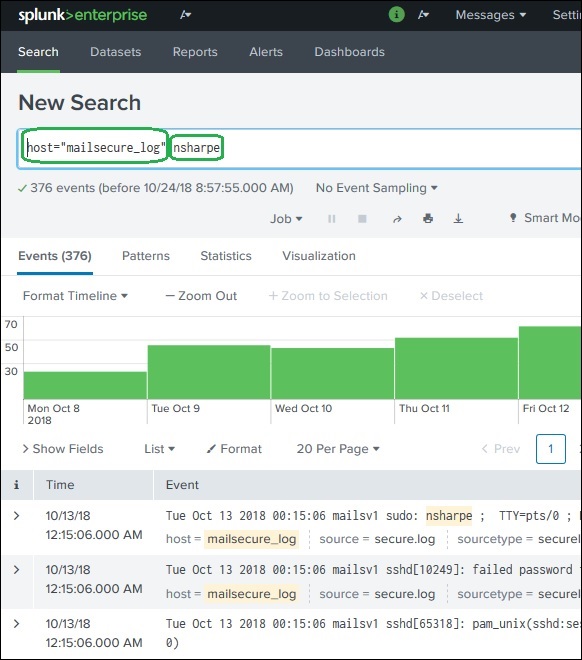
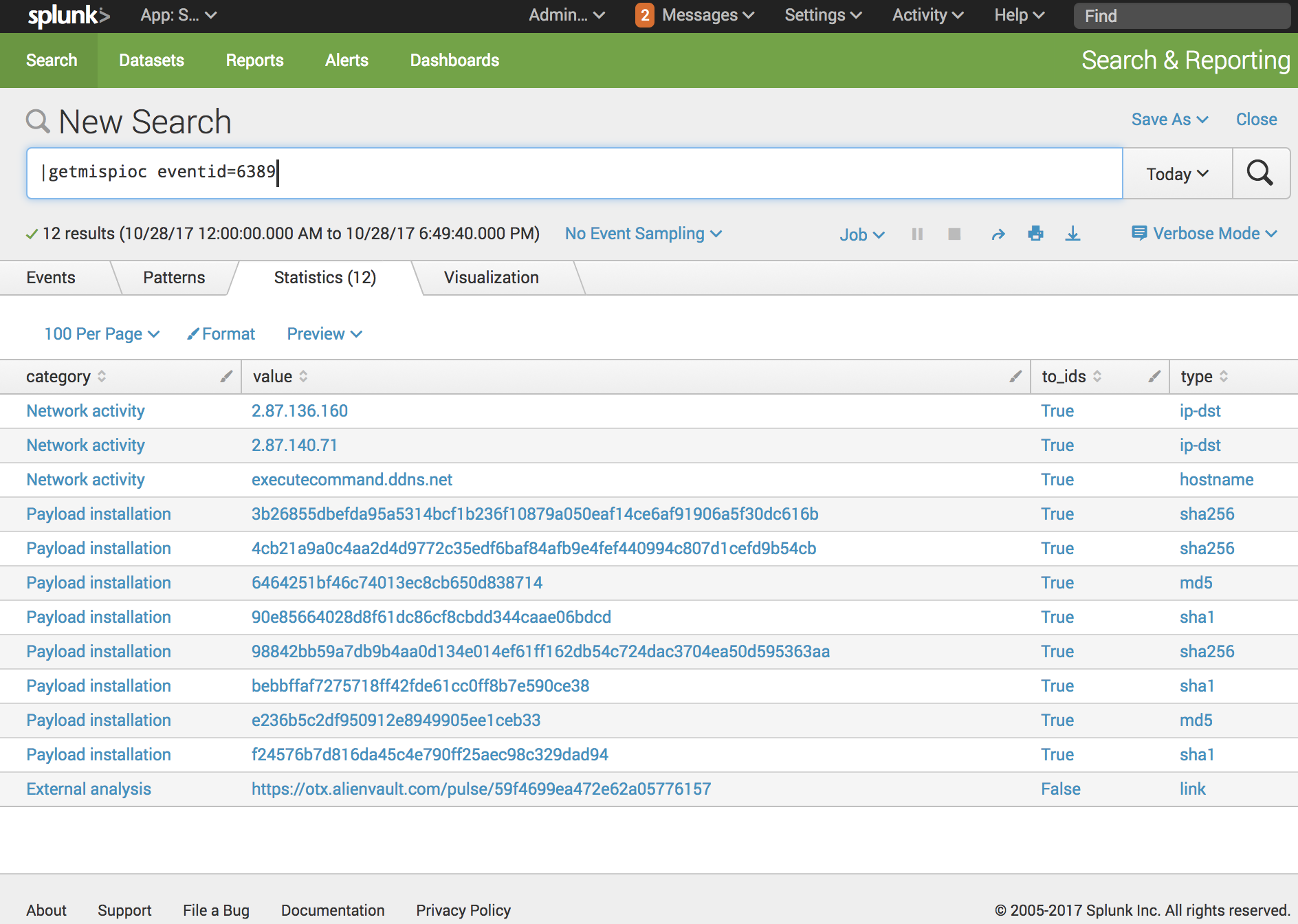
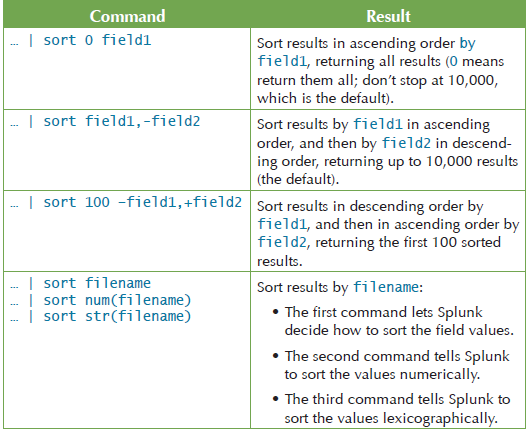
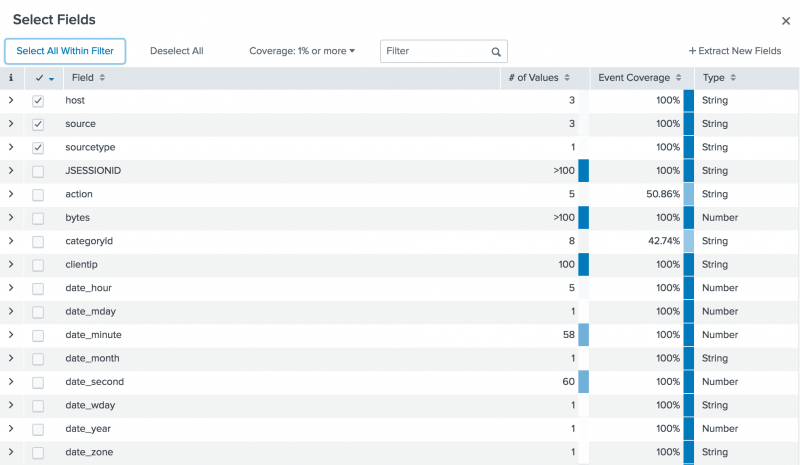
splunk search tutorial - "This website is not affiliated with Splunk, Inc. and is not an authorized seller of Splunk products or services."
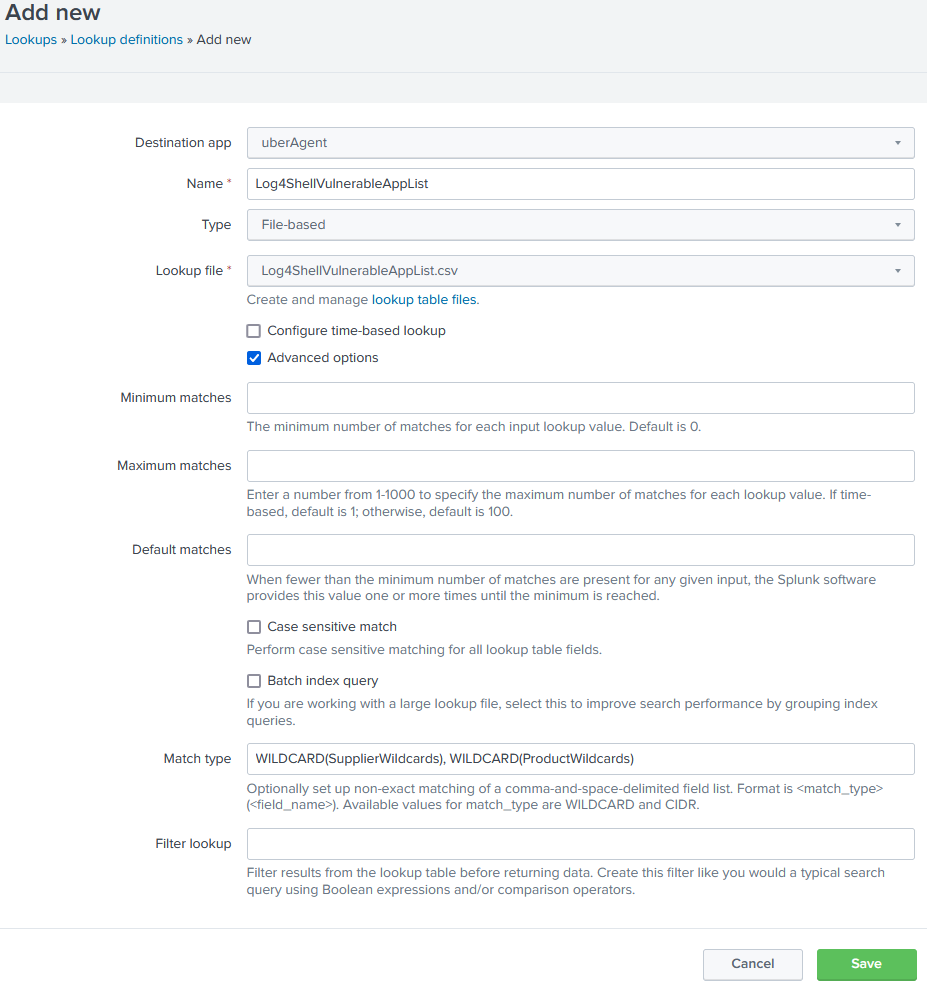
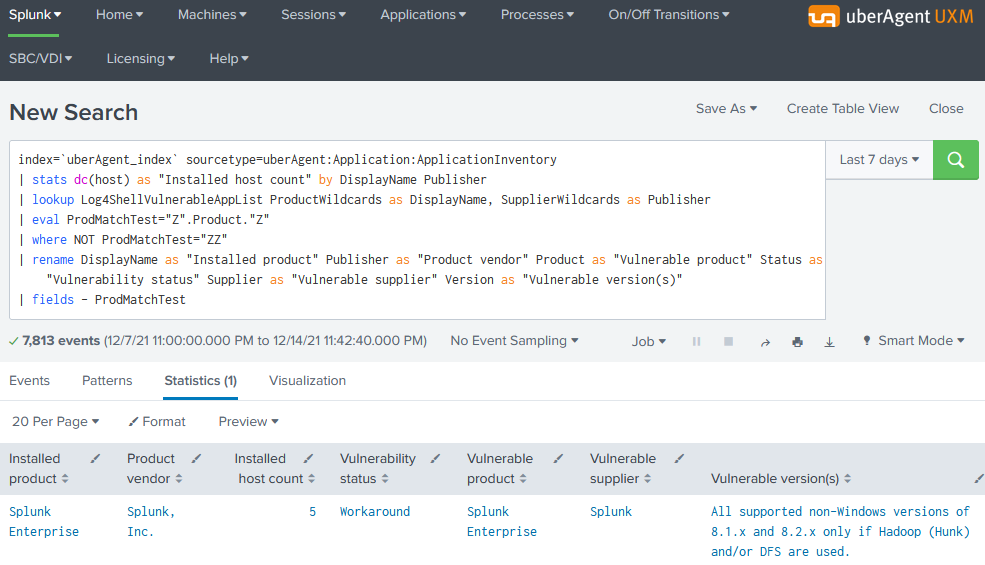
Log4Shell (CVE-2021-44228): Splunk Searches for Detecting Vulnerable Applications • UX monitoring & endpoint security analytics for Windows, macOS, Citrix, VMware on Splunk